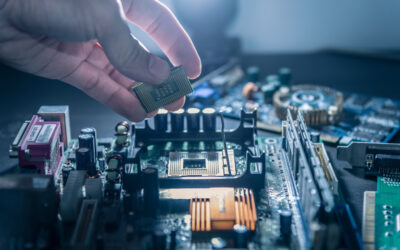
Certain models of counterfeit IT hardware are so convincing that even experts struggle to identify them as fake. Off-brand hardware isn’t inherently...
Articles
The Subtle Dangers of Outbound Spam
Outbound spam is increasingly becoming a nuisance in most organizations running their businesses online. Unfortunately, most ISP users are not aware...
Online Reputation Management: The Internet is Forever!
We are in a world where online reputation management has become critical in the employment sector. Many businesses must now screen the social...
Small Business Strategy: What Small Businesses Can Learn from Big Ones
Learning from big companies is a small business strategy that can help improve your startup’s productivity. According to Fortunly, 30.7 million...
5 Consequences of a Data Breach in Your Business
Data breaches are becoming increasingly common in today’s world. As businesses strive to improve data security to mitigate the risk of data loss,...
How IT Security Applies to Your Office Printer
Data security is an integral part of any office setting. Both your own sensitive information and that of your clients must stay private at all...
3 Industries that Need Cyber Insurance
When it comes to cybersecurity, most businesses rightly focus on preventive measures and heightened security. Unfortunately, no security system is...
4 Reasons to Develop a Mobile App for Your Business
As a business owner, you’re always looking for ways to promote your brand and attract more customers. You’re investing plenty of time and effort in...
How to Tell if Your IT Setup is Outdated
Technology-focused businesses pride themselves on having the latest and greatest the IT industry has to offer. However, some business owners may not...
Was That Security Threat an Inside Job? Here’s How to Prevent Another One
The majority of data breaches originate outside the affected organization. However, an alarmingly large minority of these cases come from inside the...
How an Unsecured Wifi Leaves Your Business Vulnerable
In an internet-driven world, customers tend to expect free, high-speed wifi from most businesses. Setting up a wifi hotspot will certainly attract...
4 Advantages of Security Cameras in Your Office
It seems that no modern office surveillance system is complete without security cameras. An employer’s reasons for installing security cameras may...
3 Reasons Not to Set Up Your Business Technology Yourself
DIY projects certainly have their appeal. There’s something satisfying about completing a task on your own, both saving money and getting a sense of...
3 Advantages of Long-Term Teleworking
The work-from-home phase for many employees shows no signs of ending shortly. With this drastic shift in the typical workday, employers are...
3 Social Engineering Attacks to Recognize
In the security field, the term “social engineering” refers to strategically employing deceptive activities to trick people into revealing sensitive...
Where do you go
from here?
Reach out and find out how great Enstep support can be!